Today, web apps are used for everything from social media to online shopping, and maintaining their security is crucial. But how can we ensure they’re safe from hackers? One of the most effective way is to use security testing tools, such as ZAP (Zed Attack Proxy) and Burp Suite. ZAP is a beginner-friendly tool that helps identify vulnerabilities in web applications, allowing us to address security flaws before attackers can exploit them. By integrating ZAP into our testing process, we can take proactive steps to safeguard our applications from potential threats.
What is ZAP?
ZAP is a free and open-source tool used to find security vulnerabilities in web applications. It acts as a “man-in-the-middle proxy” between your browser and the web application, capturing traffic and identifying security flaws in the web application. ZAP helps to uncover vulnerabilities such as SQL injection, Broken Authentication, Sensitive Data Exposure, Broken Access Control, Security Misconfiguration, Cross-Site Scripting (XSS), Insecure Deserialization, Components with Known Vulnerabilities, and Missing Security Headers. Whether you’re a developer, tester, or security enthusiast, it is designed to be user-friendly, especially for beginners like us!
Why Should You Use ZAP?
- Free and Open-Source: It’s completely free to use, making it accessible for everyone.
- User Friendly: It have an easy to use interface, even if you re new to security testing. It dosen’t need a lot of technical knowledge.
- Automated Scans: Zap can automatically scan a website to find common vulnerabilities.
- Manual Testing: As you get more comfortable, you can use ZAP’s advanced features to manually test for security vulnerabilities.
Key Features
- Passive Scanning: ZAP passively analyzes the traffic between the browser and the web application, identifying issues without actively attacking the application.
- Active Scanning: This involves actively probing the web application for vulnerabilities, such as SQL injection, XSS, etc.
- Fuzzing: ZAP can perform fuzzing to test how the application handles unexpected or malformed input.
- Scripting: Scripts can be written to enhance ZAP’s functionality or automate tasks, providing more efficient and customized security testing.
- Report Generation: After conducting scans, users can easily generate customizable reports in various format to summarize the findings.
How to Install and Configure ZAP
- Download and Install: You can download OWASP ZAP official website. It has installers for Windows, Linux, and macOS. Note that zap requires Java 11+ in order to run. You can download java from Oracle JDK download page.
- Configure Your Browser: After installation, you’ll need to configure your browser to use ZAP as a proxy. Go to Tools > Options > Network > Local Servers/Proxies in ZAP. Typically, you will set the browser proxy to
localhostand port8080(default). Next, go to Firefox’s manual proxy configuration settings and set it to use ZAP as a proxy for capturing active and passive scans. - Install Dynamic SSL Certificate: To intercept and decrypt HTTPS traffic effectively, your browser must accept ZAP’s Dynamic SSL Certificate. In ZAP, go to Tools > Options > Network > Server Certificates, then download and save the certificate. Import this certificate into your browser to avoid SSL errors during testing.
- Start Testing: Once the configurations are complete, input the target application’s URL into ZAP’s interface to begin testing. ZAP will intercept the web traffic, allowing you to analyze requests and responses for potential vulnerabilities.
Automated Scan
Automted scan are fast & efficient and prosess large applications quickly. They are perfect for routine inspections because they cover a broad range of vulnerabilities and produce comprehensive findings sorted by severity.
To perform an automated scan,
- Click on the Quick Start tab -> Automated Scan button.
- In the URL to attack text box, enter the full URL of the web application that you want to test.
- Click on the Attack
Note: When security testing any web application, make sure that you have authority to test it or that it was created specifically for security testing.
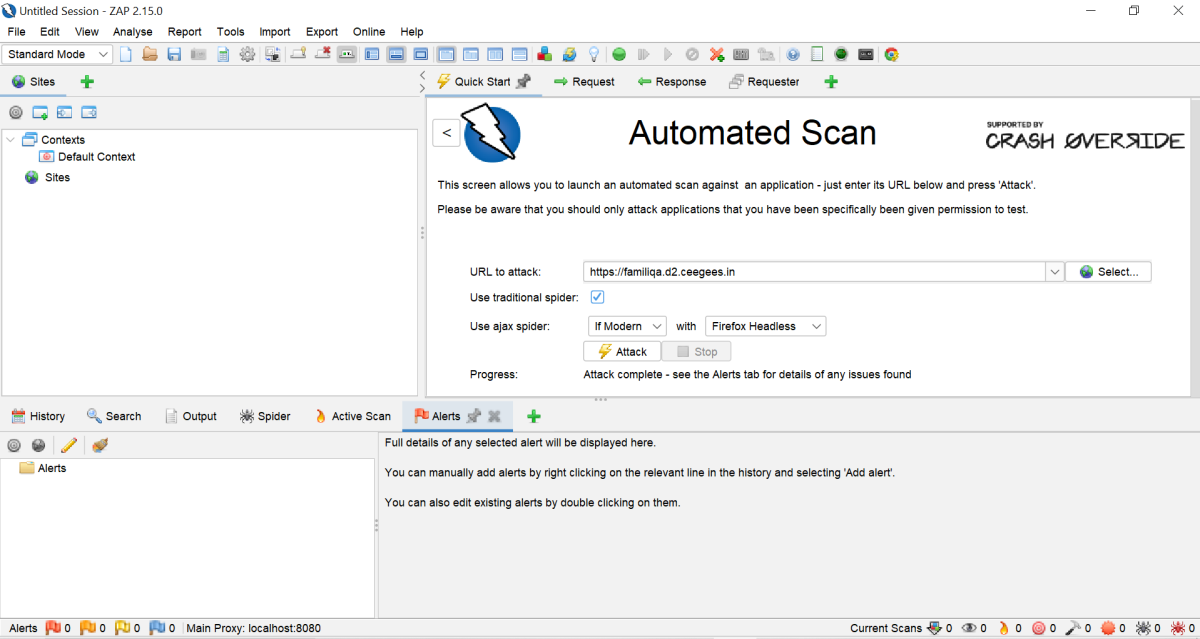
- All vulnerabilities discovered during the scan appear in the alerts tab and are displayed by their severity. You can double click and expand the alerts.
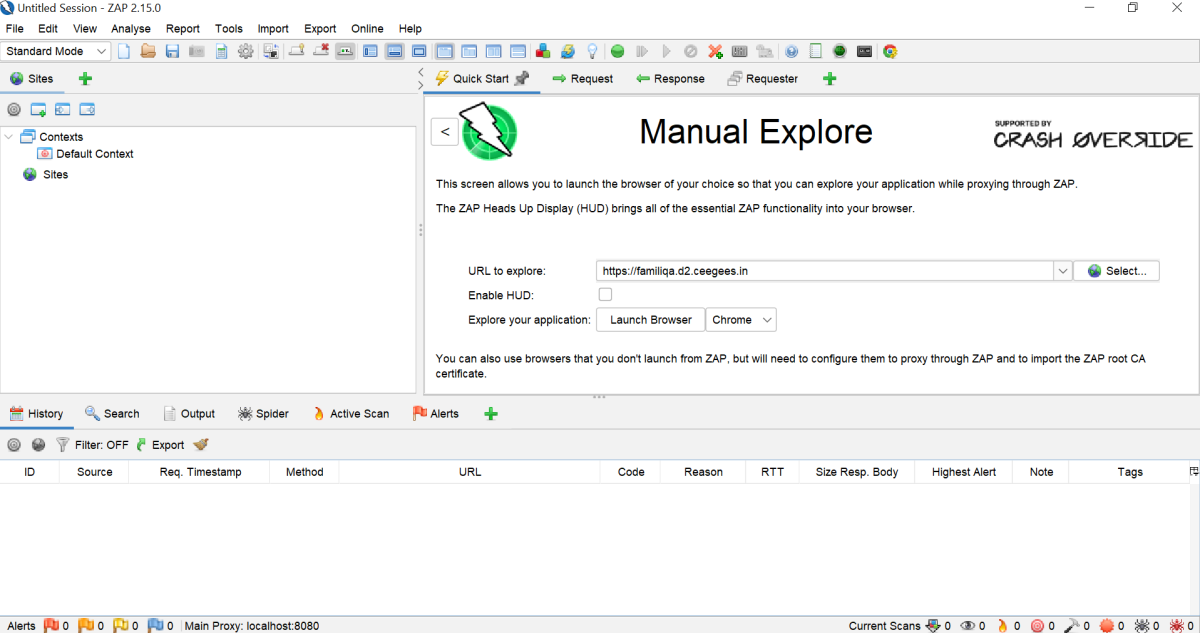
Manual Explore
Manual exploration in Zap involves human testers, so it provides enhanced contextual awareness, identifies complex vulnerabilities, and replicates actual user behaviour, all of which contribute to a more accurate discovery of security flaws.
To Manually Explore your application:
- Click on the Quick Start tab -> Manual Explore button.
- In the URL to explore text box, enter the full URL of the web application you want to explore.
- Select the browser you would like to use and click on Launch Browser.
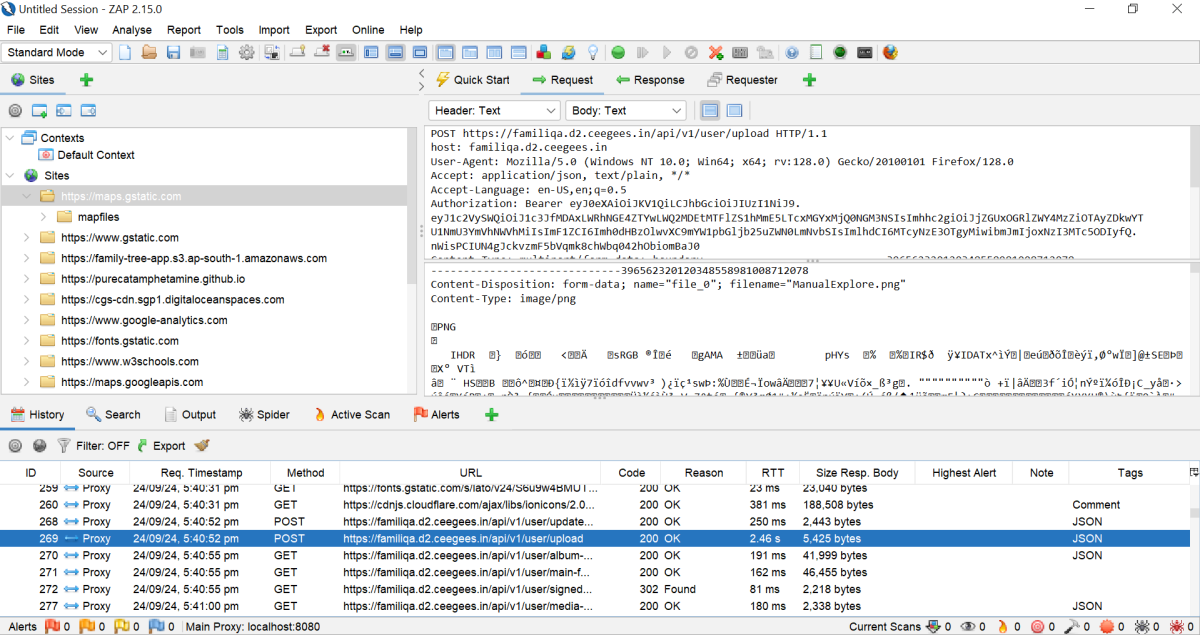
- Manually browse through the web application. Log in to the application (if needed). Then navigate through different sections, submit forms, and perform actions that users would typically do.
- Monitor the
SitesandHistorytabs to see the recorded interactions.

Conclusion
ZAP serves as a valuable tool for both beginners and experienced security testers, providing robust capabilities for identifying vulnerabilities and strengthening application defenses. Through passive and active scanning, fuzzing, and the ability to customize functionality with scripts, ZAP empowers users to conduct thorough security assessments. By integrating ZAP into your testing workflow, you can proactively address potential threats and enhance the overall security posture of your web applications. As we continue to navigate the complexities of online security, tools like ZAP will remain essential in our efforts to protect against evolving cyber threats.
QA Analyst
